The same-origin policy is an important concept in the web application security model. The policy permits scripts running on pages originating from the same site.
I found that users using FlashFirebug are vulnerable to same-origin policy bypass. This Firefox add-ons create a files on the Flash Player Trust directory disallowing same-origin policy.
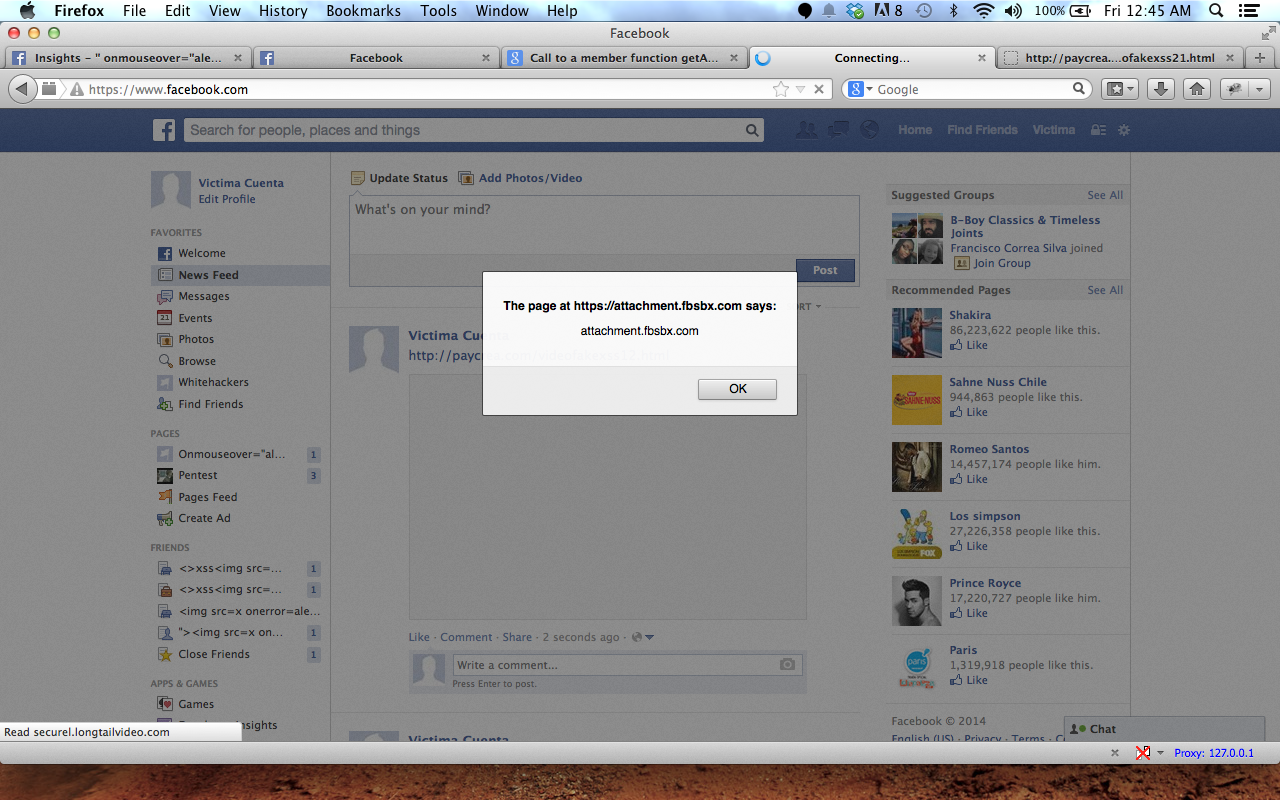
For this example I will use Facebook Video preview box to trigger this Flash XSS. (Fortunately Faceboook use attachment.fbsbx.com )
By using a Flash XSS plus having FlashFirebug install on the Victim Firefox I can trigger this XSS and bypass Same Origin Policy
I report this to Facebook and this was the response:
And me as a good bounty hunter I report to Adobe:
After doing a bit of looking I found that o-minds.com have a report bug page and here is their response:
I reply to them and after that I didn't receive a response.
My conclusion:
External Addons can bypass Flash "Same Origin Policy" by adding a files to flash trust directory allowing all Script Access ignoring the Same Origin Policy and this happen without the user knowledge.
Video Poc:
Status:
This bug still works and apparently is not geting fixed soon.