Google Webchat | Cross Site Scripting Vulnerability
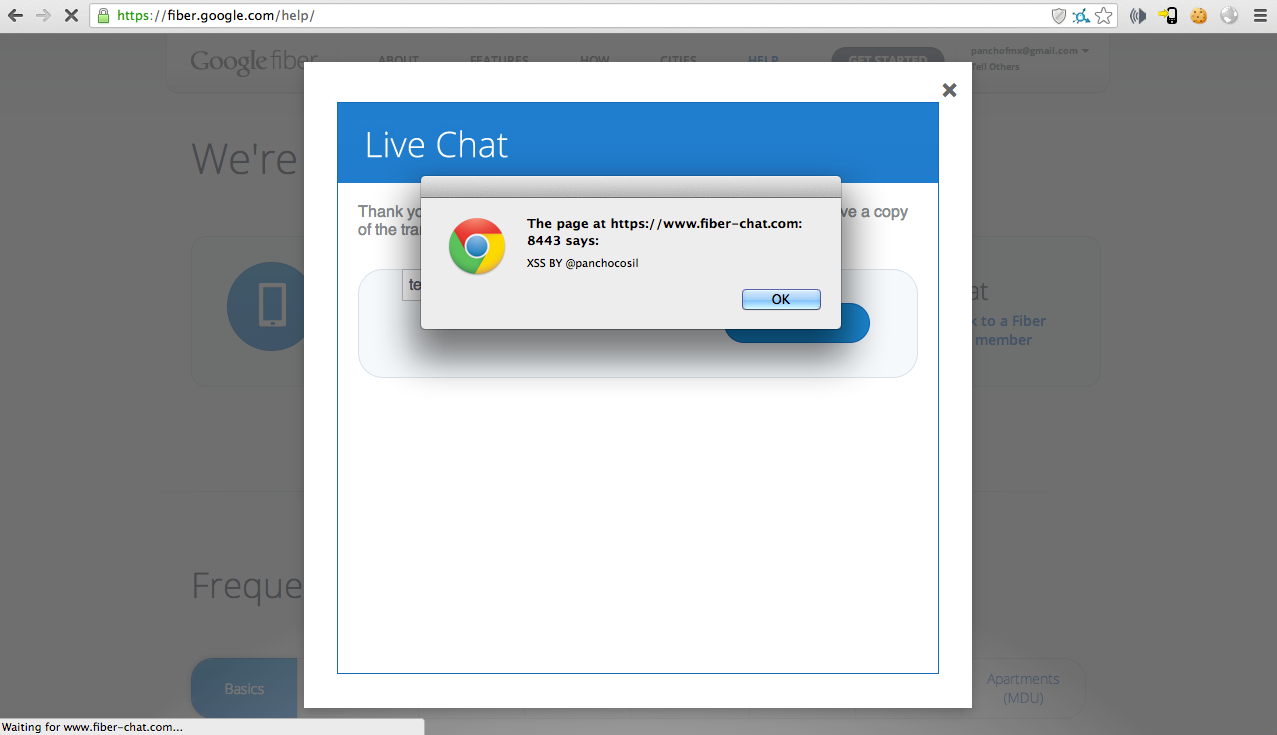
I find out that fiber.google.com was using a third party app at fiber-chat.com:
Turned out that the email parameter was vulnerable to XSS
I Report this to Google Security Team and the response was this:
Report: Tue, Jun 18, 2013 1:34PM
Fix: Wed, Jun 19, 2013 9:00AM
No Reward for this Bug
I find out that fiber.google.com was using a third party app at fiber-chat.com:
Turned out that the email parameter was vulnerable to XSS
test@gmail.com"><svg/onload=alert(1)>
When Login off the chat I got a positive XSS response.
I Report this to Google Security Team and the response was this:
Report: Tue, Jun 18, 2013 1:34PM
Fix: Wed, Jun 19, 2013 9:00AM
No Reward for this Bug